Introducing Firewall
Firewall is a comprehensive network security solution for the IBM i (AS/400). It completely secures your system against external threats initiated via the network and controls permitted user activities after access is granted. Firewall is a robust, cost-effective security solution.
Firewall is by far the most intuitive and easy-to-use IBM i security software product on the market. Its top-down functional design and intuitive logic creates a work environment that even novices can master in minutes.
Although Firewall was not designed to protect your command line usage. It will secure STRSQL command line usage for various tables.
Why is Firewall Necessary?
Originally, the IBM i was used almost exclusively in a closed environment, with host systems connected to remote data terminals via proprietary technologies. Within this closed environment, the security features of the IBM i operating system provided the strongest data and system security in the world. User profiles, menus and object level security provided all the tools necessary to control what users were allowed to see and do.
In today's world of enterprise networks, laptops, distributed databases, the Internet, and web technologies, closed computing environments are basically extinct. Technological advances compelled IBM to open up the IBM i and its operating system to the rest of the world. This openness brought along many of the security risks inherent in distributed environments. System administrators need to equip themselves with a new generation of security tools to combat these evolving threats. Firewall is that solution.
Feature Overview
Top-Down Security Design
Top-Down security design means that the process of designing and applying security rules follows the most efficient logical path possible. The user formulates a minimal number of rules for achieving maximum security and the system applies these rules to transactions. The unique design behind Firewall leads to checking far fewer transactions than competitive products. This saves planning and maintenance time as well as valuable system resources.
Top down security offers a simple hierarchy of rule types. When a higher level rule type fully meets a situation's security requirements, the user doesn't have to formulate additional rules for the particular situation.
Server Security
System i security is based on four basic levels:
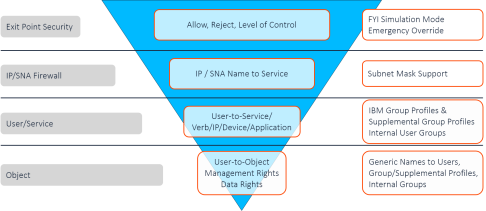
- Server/Exit Point Security
- TCP/IP Address Firewall Security
- User-to-Service Security
- Object Security
Simply put, whenever a higher, less specific rule will suffice, you do not need any more specific rules. For example, if you do not need to use FTP, you simply reject all transactions at the FTP Server/Exit Point level. You do not need to define any rules that limit FTP access via specific IP addresses, by specific users, or to specific objects.
Logon Security
Logon security uses a similar set of levels, tailored to the specific requirements for logging in:
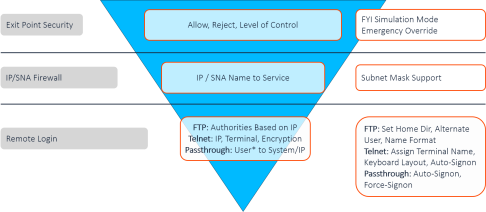
- Server/Exit Point Security
- IP/SNA Firewall
- Remote Login Security
Multi Thread Support
Calling programs from threads other than the main one forces limitations on the called programs. For example, the command Override with Data Base File (OVRDBF) cannot be used. This requires special programming in the called program.
Firewall secures network access by providing programs to be called by security related exit points. Firewall modules have been specifically designed to improve their capability to work in secondary threads when the relevant system APIs can use them.
We recommend, when possible, working in single thread mode. Otherwise, perform a check, such as checking the log, in order to validate proper performance.
Firewall Rules and the Best-Fit Algorithm
Firewall is a rules-based security product. The user creates a wide variety of rules to cover many different situations and to counter different kinds of threats. Some rules will likely apply globally to all or most activity types while others will cover very specific situations.
FYI Simulation Mode
Using FYI Simulation Mode, you can simulate the application of security rules without physically rejecting any activity. All “rejected” transactions are recorded in the Activity Log as such but the activity is allowed to proceed without interruption. With this feature, you can test your rules under actual working conditions without adversely affecting user access.
FYI Simulation Mode may be enabled globally for all activity or enabled for individual function servers to test security rules for those servers without affecting rules that apply to others.
Emergency Override
With the Emergency Override feature, you can temporarily override all existing security rules, allowing or rejecting all activity. This feature is useful when you need to respond quickly to emergencies such as critical transactions being rejected due to problems with Firewall security rules or a sudden security breach.
Rule Wizards
The unique Rule Wizards feature makes security rule definition a snap, even for non-technical system administrators. With this user-friendly feature you can view historical activity together with the security rule currently in effect on a single screen. You can even modify the existing rule or define a new rule without closing the wizard. The Rule Wizards are an invaluable tool for defining the initial set of rules after you install Firewall for the first time.
Logging
The activity log provides complete details for every transaction captured as a result of a security rule. The user can select the activities to be included in the Activity Log and the conditions under which they are logged. You can display or print selected records from the Activity Log by entering the Display Firewall Log command (DSPFWLOG) on any command line or from numerous locations on Firewall menus and data screens.
For REJECTED transactions - The log entry shows the first level where the request is a violation to the Firewall rules.
For ALLOWED transactions - The log entry shows the last test that was taken and found valid.
No user, including QSECOFR, can update or delete records from the file that contains the log. This is true even when using SQL, DFU, and CHGFC command and so on.
Authorized users can:
- Set the number of days that data is kept online.
- Change the logging options for individual servers (exit points).
- Change the logging options per user.
Query Wizard
With the powerful Query Wizard, you can design custom output reports that show exactly the data you need without programming or technical knowledge. You can create query definitions by using a series of simple parameter definition screens. Output may be a printed report, a screen display, or a text, HTML, or PDF file saved on the System i.
Using highly detailed filter criteria, you can select only the records you need by using Boolean operators and the ability to combine complex logical conditions. Firewall's flexibility enables you to specify the sort order according to multiple fields. All reports can run automatically and be e-mailed to the system administrator.
The "User-Centric" Approach
Firewall has a "user-centric" approach set in the top-down model, which helps the security administrator to manage user security easily and efficiently and reduces the number of security rules.
Raz-Lee Security has created two new user groups in addition to the existing general Firewall group. Together they form three groups that enable organization of the users: General Groups, Application Groups, and Location Groups.
User Security
Firewall offers optimized basic user security. You can create a single user security definition in several ways:
%Groups
Assign a user to a user group (similar to the option of selecting members for each of the user groups).
Services
Same as the previous method of user-to-service definitions
IP
Same as the Location group rules, but only applicable to single users.
Device Names
Only for Telnet sign on. Same as Location group rules, but only applicable to single users
Intrusion Detection
This feature enables Firewall to trigger proactive responses (similar to the ones available on the Action module but less flexible). Those important responses, such as notification about intrusions to the admin by MSGQ and email are general and easy to use.
Native IBM i Text Based User Interface
Firewall is designed from the ground up to be a user-friendly product for auditors, managers, security personnel and system administrators. The user interface follows standard System i CUA conventions. All product features are available via the menus, so users are never required to memorize arcane commands.
Many features are also accessible via the command line, for the convenience of experienced users.
Menus
Product menus allow easy access to all features with a minimum number of clicks. Menu option numbering and terminology is consistent throughout this product and with other Raz-Lee products.
To select a menu option, simply type the option number and press Enter.
The command line is available from nearly all product menus. If the command line does not appear (and your user profile allows use of the command line), press the F10 key to display it.
Commands
Many Firewall features are accessible from any command line simply by typing the appropriate commands. Some of the most commonly used commands are.
- Display Firewall log (DSPFWLOG)
- Run a Firewall query (RUNFWQRY)
- Run a predefined group of reports (RUNRPTGRP)
- Display Firewall user activity (DSPFWUSRA)
Data Entry Screens
Data entry screens include many convenient features such as:
- Pop-up selection windows
- Convenient option prompts
- Easy-to-read descriptions and explanatory text for all parameters and options
- Search and filter with generic text support
