Chapter 22: Administration
FileScope includes security functions that prevent the unauthorized use of your files and allows you to trace activity performed on your files.
FileScope consists of two main companion commands:
-
SHWFC (Show File Contents) - to view or print.
-
CHGFC (Change File Contents) - to change, view or print.
Therefore, using the System i standard authorization system, authorities can be given separately to the change and show functions.
-
The CHGFC command is completely separate from the SHWFC command and can be removed from the system altogether if so desired.
A file security system is included. Sensitive data can be protected from being updated or displayed by unauthorized users.
Sensitive capabilities can be blocked. Command parameters control selection of new files and Viewpoint manipulation. This enables selective implementation of FileScope's abilities through menus.
File Access Security
-
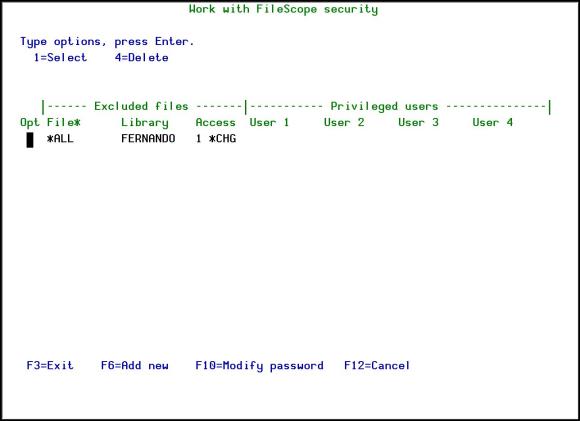
Select 21. File access security in the main FileScope menu, the Work with FileScope security screen appears
-
The Access Security System prevents the use of the FileScope on files or libraries. For example, it can prevent the use of CHGFC (Change File) or even SHWFC (Show File); it can prevent the use of all files beginning with XYZ which are located in a specific library or in any library.
In addition, there is a possibility to define a group of privileged users who are not concerned by the pre-defined restrictions!
The WRKFSSEC command provides access to an internal security system enabling definition of files to be protected from access.
A list of privileged users (those who are allowed to use this file) can be defined.
-
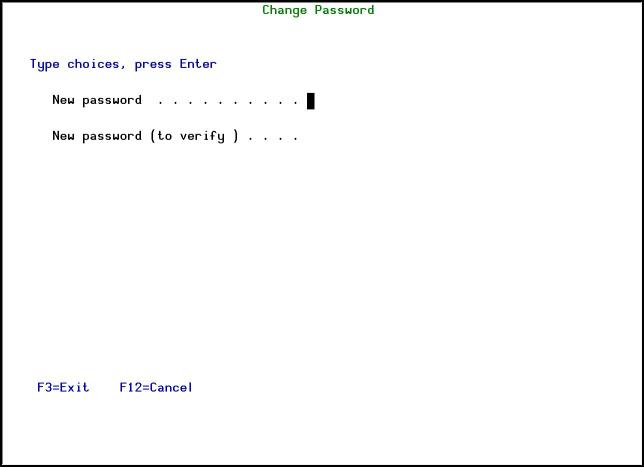
The security system is protected by an internal password. The default password is QSECOFR. It is recommended to modify it by using F10 - modify password.
-
Press F6 in the Work with FileScope security screen to add a new file.
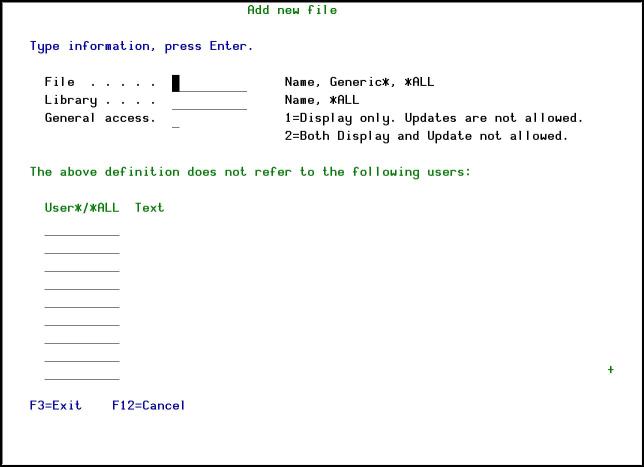
FILE AND LIBRARY
Denied files can be specified as:
-
Specific file (full or generic)
-
All files in a library
-
A file name regardless of which library contains it
-
All files in all libraries
DENIED ACCESS TYPE
Two levels of security can be defined as follows:
-
prevent use of CHGFC command (updates)
-
prevent use of all FileScope commands
PRIVILEGED USERS
A list of users, excluded from the restriction, can be defined. Generic user names can be authorized.
TECHNICAL ASPECTS
Specific rules (without *ALL) are more important than general rules.
Security exists in the following sequence:
-
Specific file name and library name.
-
Specific file name in any library.
-
Any file in a specific library.
-
All files in all libraries.
If the CHGFC command is attempted, a check is first done to search for a restriction of CHGFC use (level 1) and then for a general restriction.
Command Authorization
FileScope consists of two commands:
-
SHWFC (Show File Contents) - to view or print.
-
CHGFC (Change File Contents) - to change, view or print.
Therefore, authorization for command usage can be granted for the change function separately.
The CHGFC command is totally separate from the SHWFC command and can be removed from the system altogether if so desired.
Logging
All users of the product are logged, along with the user details and the time of use.
Working with Trace
Available in FileScope Platinum only
The Trace Security System (WRKFSTRC command) follows up on the use of your files. All FileScope operations can be registered on FileScope internal files. This enables you to follow up on each and every user action.
This follow-up system is based on three different levels:
-
BASIC: basic information on users and file use
-
ADVANCE: add information on the update request definition (increase the price product by 10%)
-
AUDIT: all the above information in addition to a separated print list that indicates all field changes on each record
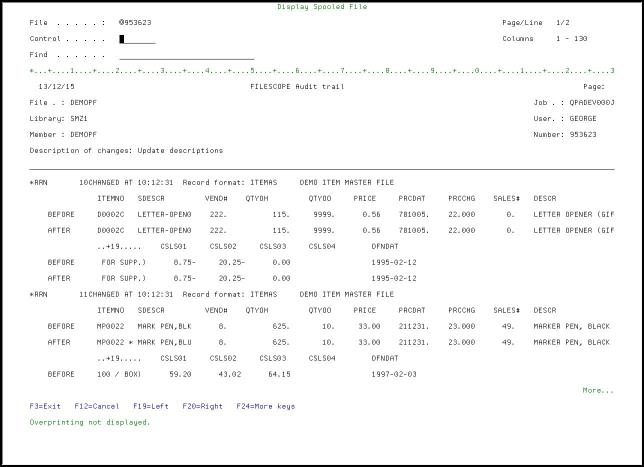
You set the level with the Run trace (*BASIC, *ADVANCE, *AUDIT) parameter. To see details of how to set this parameter, see Undo and Auditing (SOX) on page 1.
-
Select 22. Trace and Audit from the FileScope Main menu. The Work FileScope Trace screen appears.
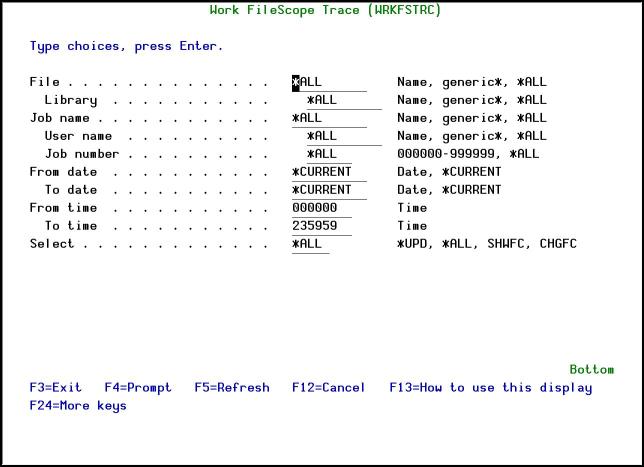
-
If the Run Trace parameter was set to *AUDIT, the option 5=Audit trace can be selected in the Opt field.
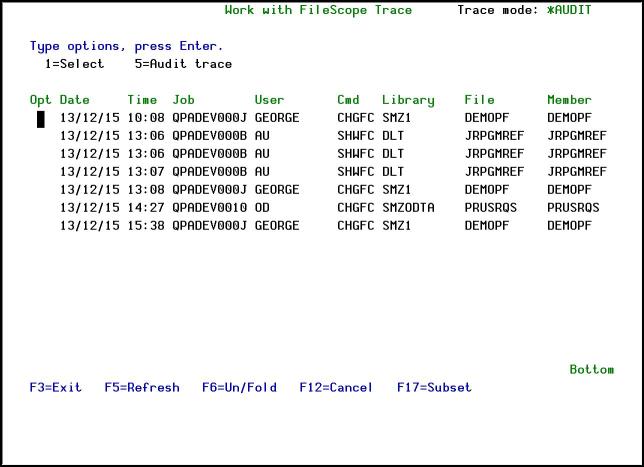
The following screen is an example of an *AUDIT panel where you can see the updated records before and after the changes, the updated fields (proceeded by a “*”), the description of changes and more.