Creating and Modifying Firewall Rules
When a user requests access to an exit point on the IBM i, coming either from within the system or outside of it, Firewall uses its layered security model to test whether the access should be accepted or rejected.
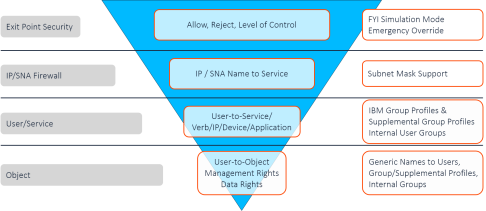
It first checks whether access to the exit point itself is allowed.
If that is accepted, it checks whether access from the IP or IPv6 address or SNA system name requesting incoming access or to the IP address to which the user is requesting outgoing access is allowed.
If that is also accepted, it checks whether the specific user, or the group to which the user belongs, is allowed to access that service.
Finally, if that is accepted, it checks whether access is allowed to the native or IFS object on the system is allowed.
The request is only accepted if it has passed all four layers of checks. If it fails any check, it is rejected without the need to check the layers further in.
| GSFWPMNU Firewall iSecurity System: RLDEV Basic Security Analysis 1. Activation and Server Settings 41. Log, Queries, What-If Analysis 2. IP, Systems Basic Filtering 42. Reporting of Definitions 3. Users and Groups 4. Native Objects 45. Rule Wizards 5. IFS Objects 46. Test Security Rules Additional Control 11. FTP/REXEC 12. Telnet 13. Passthrough Maintenance 14. DDM, DRDA, SSH, Port... 81. System Configuration 15. Incoming/Outgoing Socket Connections 82. Maintenance Menu 17. Free Style Rules 89. Base Support 18. PC Application Security Selection or command ===> F3=Exit F4=Prompt F9=Retrieve F12=Cancel F13=Information Assistant F16=System main menu |
You can create and modify the rules used to filter access at each level from the Firewall Main Menu (STRFW).
- To create and modify rules based on exit points, select 1. Activation and Server Settings from the Firewall Main Menu. The Activation and Server Settings screen appears, as shown in Setting Firewall Rules by Server.
- To create and modify rules based on IP and IPv6 addresses and remote system names, select 2. IP, Systems Basic Filtering from the Firewall Main Menu. The Work with Dynamic Filtering screen appears, as shown in Setting Firewall Rules for IP Addresses or System Names.
- To create and modify rules based on users and groups, select 3. Users and Groups from the Firewall Main Menu. The Work with Users screen appears, as shown in Setting Firewall Rules for Users and Groups.
- To create and modify rules based on native objects, select 4. Native Objects from the Firewall Main Menu. The Native Object Security screen appears, as shown in Setting Firewall Rules for Native Objects.
- To create and modify rules based on IFS objects, select 5. IFS Objects from the Firewall Main Menu. The IFS Security screen appears, as shown in Setting Firewall Rules for IFS Objects.
- To create and modify rules for PC applications accessing the system, select 18. PC Application Security from the Firewall Main Menu. The Work with Client-Application Security screen appears, as shown in Securing PC Client Applications.
- To display definitions and to change rules for users, groups, and addresses, select 42. Reporting of Definitions from the Firewall Main Menu. The Definitions screen appears, as shown in Displaying Definitions and Changing Occurrences of Users and Addresses.
