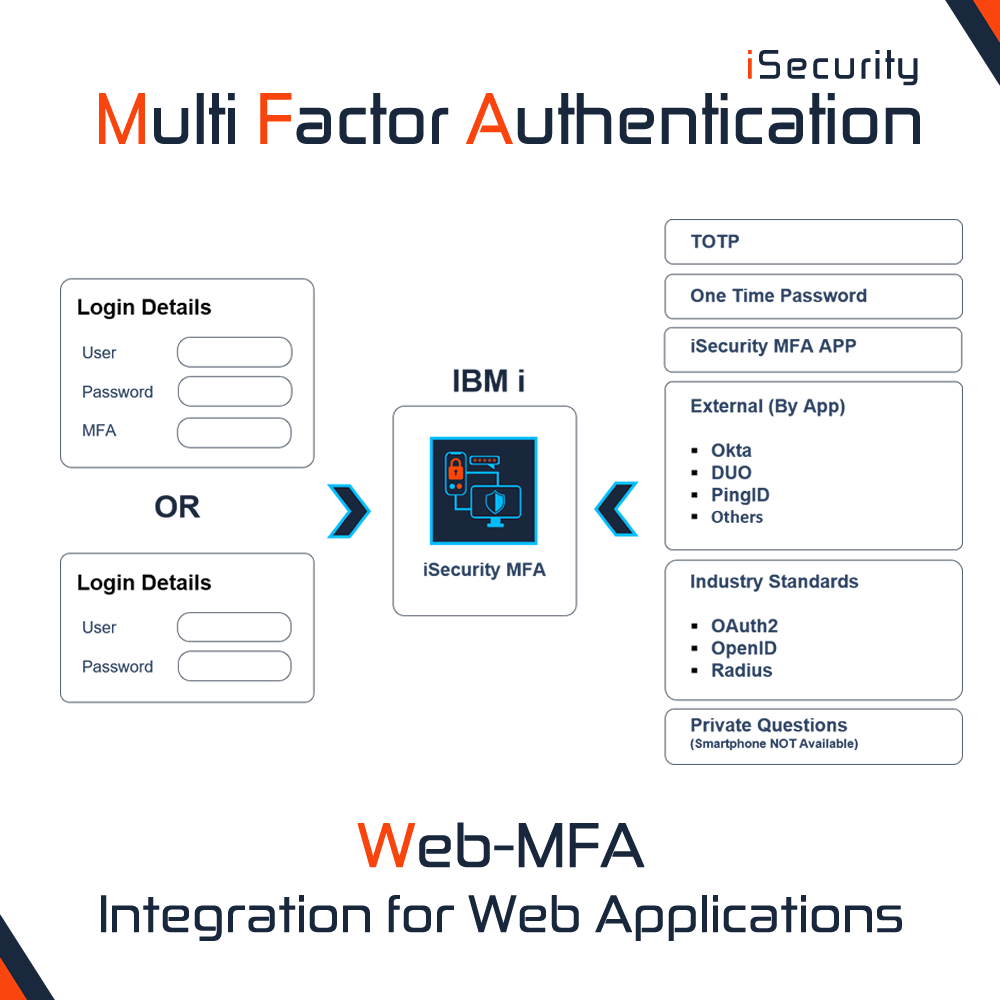
New Feature: Web-MFA Integration for Web Applications
Raz-Lee Security introduces Web-MFA, a powerful new enhancement to iSecurity Multi-Factor Authentication (MFA), designed to extend strong authentication beyond IBM
Ransomware attacks on IBM i and viruses spread by the IFS require special attention. Such attacks damage companies to the extent that they have to seize their activities.
iSecurity helps companies meet their IBM i security and regulatory requirements in this area.
Detects and isolates the threat, and prevents it from damaging valuable data.
IFS virus checks and scans, Native Object Integrity checks, alert by email and by Syslog.
Gives to you the power to choose the Antivirus Database Provider.
Comprehensive virus detection by marking, quarantining, and deleting infected files, and prevents AIX becoming an infection source.
Makes automation and orchestration tasks easier for your iSecurity Products on the AIX Servers.
.
iSecurity Auditing products help companies meet their IBM i auditing requirements by providing best-in-class reporting and monitoring solutions that secure their business-critical databases.
Real-time monitoring for QAUDJRN, QIPFILTER, QIPNAT, QACGJRN, QQOS, QSNMP, QDSNX, QVPNQZMF, QHST User Activity and more. Schedule Reports and Security status.
Audit by recording of 5250 screen activity for end-to-end audit trails with search and playback capabilities.
Automatic tracking of changes to production libraries with the sources used to create the programs.
Stay in compliance. Plan, Check and Set parameters and authorities of User Profiles, Native Objects and IFS.
Proactive response in real-time to any security event by Email, SMS, Syslog, SNMP, and CL script processor.
Real Time System monitoring supplied with information via the functions of the iSecurity Audit module.
Each module in our comprehensive security solutions for IBM i is designed to work independently or collectively to secure remote access, control user authorities and secure objects.
Column-level field encryption based on IBM’s FIELDPROC, Encryption & Tokenization.
Private and Public key technology for encrypting data files end-to-end.
Effective Protection against any situation that could compromise security and reliability for IBM i. Native Firewall Solution to control every Exit Point, besides control for Commands and Updating Files in Software Development Environments.
Network security, controlling Exit Points, Open DB’s and SSH. Rule Wizards and graphical BI.
Control validity of System and User commands and their parameters, per user, IP, time, etc.
Regulates update files in production libraries. It provides a new security layer.
Raz-Lee has developed several evaluation, reporting and alert solutions for assessing security risks, analyzing data and presenting actionable information to help executives, managers and other corporate end users make informed business decisions.
Easy to define and integrate with IBM QRadar, Tivoli, RSA, ArcSight, and more.
Intuitive Graphical BI analysis of security data, supports “drill” to specific events.
iSecurity GUI makes it easier for even non-IBM i administrators and managers to configure and use the iSecurity Suite of solutions.
Single view for Network-wide PCI, site-defined compliance checks for multiple LPARS.
Analyzes and scores IBM i security definitions, suggests corrections and solutions.
Works with IBM’s Authority Collection data. It reads, summarizes and analyzes users.
Real-time DB activity including READ. Compares values by fields, Alerts and Reports.
Standard Native access to Oracle, MSSQL/MySQL, from STRSQL, RPG, COBOL.
SOX enabled File editor with UNDO capability and Log record of Changes.

Any organization that stores, processes or transmits cardholder data is required to comply with the PCI DSS standard.

Legislative audit requirements to protect investors by improving the accuracy and reliability of corporate disclosures

A group of regulations that combat waste, fraud, and abuse in health care delivery and health insurance.

The General Data Protection Regulation reinforces and binds together information security for all people inside the European Union (EU).

The Digital Operational Resilience Act, DORA is one of the newest mandates governing how EU financial services organizations manage IT and cyber risks.

The NIS2 Directive is structured around several key domains, each critical to bolstering Europe’s cyber defenses.
Our Development Team is always improving our products.
iSecurity Suite is Native to IBM i so no additional structure is needed.
Partnerships with major global SIEM & DAM solution providers.
Users can choose to work on Green Screen or GUI (Windows).


Raz-Lee Security introduces Web-MFA, a powerful new enhancement to iSecurity Multi-Factor Authentication (MFA), designed to extend strong authentication beyond IBM

The IBM i platform often serves as a cornerstone for business-critical operations: ERP, financials, manufacturing, healthcare systems. It stores highly
Receive our latest blog posts directly in your inbox!