ARMONK, N.Y. and MUNICH, July 8, 2025
IBM (NYSE: IBM) has unveiled IBM Power11, the next generation of IBM® Power® servers. Redesigned with innovations across its processor, hardware architecture, and virtualization software stack, Power11 is built to deliver the availability, resiliency, performance, and scalability that enterprises demand—for seamless hybrid deployment, both on-premises and in the IBM Cloud.
Power11 is engineered to be the most resilient server in the history of the IBM Power platform, with 99.9999% uptime. In combination with zero planned downtime for system maintenance and guaranteed ransomware threat detection in under one minute via IBM Power Cyber Vault, Power11 sets a new standard for business continuity—addressing both planned and cyber-incident-related downtime.
Note: The one-minute guarantee applies only to the detection alert. Remediation involves drive replacement, up to the cost of the covered product.
How Long Does Ransomware Detection Take?
The Power Cyber Vault solution is an integrated cyber resiliency tool aligned with the NIST Cybersecurity Framework. It helps identify, protect, detect, and automatically respond to cyber threats. Cyber Vault safeguards against cyberattacks such as data corruption and encryption by using proactive, immutable snapshots, which are automatically captured, stored, and tested on a custom-defined schedule.
Power11 also incorporates NIST-approved, built-in quantum-safe cryptography to help protect against “harvest-now, decrypt-later” attacks and firmware integrity threats.
Detection speed depends on the frequency of snapshots and backup intervals, which are configurable based on your business requirements. For long-term protection, Safeguarded Copy can be complemented with offline backups to virtual tape, for example, after validating an online copy.
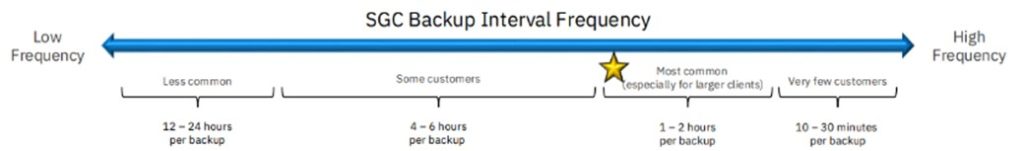
For the most common configurations, the time for Ransomware Detection is about 1 to 2 Hours.
Power Cyber Vault is an excellent infrastructure-level cyber resiliency tool, but it does not replace a real-time, IBM i-native antivirus and anti-ransomware solution. That’s why Raz-Lee’s iSecurity Antivirus & Anti-Ransomware remains essential.
How Does Raz-Lee’s Anti-Ransomware Protect Your IBM i?
Raz-Lee iSecurity is a software suite that provides advanced protection for IBM i, including granular access control, real-time alerts, comprehensive auditing, file change tracking, firewall, antivirus, and enhanced monitoring of insider threats and network/FTP activity. MFA, AOD, and other key security features are also included.
Anti-Ransomware identifies, stops, delays, and reports attacks in real time. It sends alerts to SIEM systems and managers, disconnects intruders, blocks compromised users, and minimizes the damage caused by ransomware attacks on IBM i. Its asynchronous operation significantly improves performance, preventing any noticeable delays. It also supports multithreading, as recommended by IBM. Multithreading allows a single job to manage all user shares, instead of creating one job per share—for example, 100 users with 3 shares each would otherwise generate 300 jobs.
Additionally, our Sandbox feature reduces false alerts to virtually zero. Files suspected of being compromised are passed to the sandbox, which attempts to execute them. If the execution is successful, they are deemed non-malicious—and vice versa. The sandbox runs natively on IBM i, requiring no additional hardware or software.