According to a recent AT&T work survey, “Hybrid work will be the foremost working model by 2024, with 56% of work done offsite.” Many companies that deployed remote work solutions during the pandemic found that employees working remotely can be as productive as being in the office. In addition, employees are demanding the flexibility to work where they can be most productive and content.
At the same time, cybercriminals see the expanded hybrid workplace as an increased opportunity to access company networks through weak security in employees’ homes and remote work locations. This expanded risk extends to IBM i companies where employees are connecting and logging into applications and accessing IBM i file systems such as IFS.
Top security risks include phishing schemes, insider threats and lax security that enable cybercriminals to access valid user credentials and steal corporate and customer information as well as conduct ransom attacks for IBM i companies.
Companies need to develop a hybrid work strategy and expand cybersecurity strategies by securing internal applications, cloud access, remote applications and their IBM i systems for the hybrid workplace.
Hybrid Workplace Security Concerns
Key concerns for hybrid workplace cybersecurity include:
- Secured access to company systems and information, including understanding the risks associated with VPNs and home networks
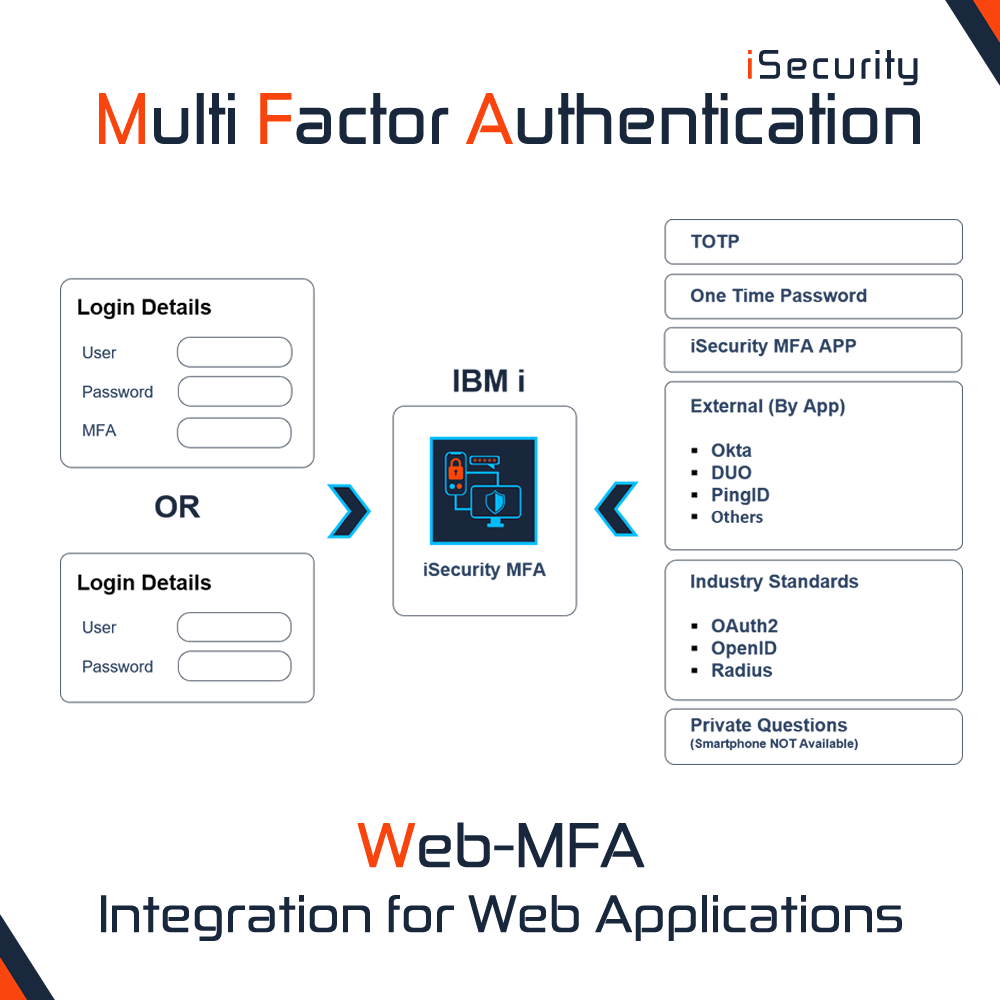
- Zero trust for identity and access management. With employees accessing company networks and systems from homes, cafes and other remote locations, the edge of the company is no longer defined by firewalls and internal networks, and a company cannot verify identify with user ID and password authentication alone. In fact, a zero trust strategy, as defined by NIST, assumes that you trust no one and utilize increased IAM solutions that support multifactor authentication and other security technologies to ensure that only those users that are authenticated and trusted can access company systems and information, including IBM i.
- Incorporating user education into your cyber strategy. Technology alone cannot ensure a secure, trusted and compliant company IT environment. Educating users about potential security risks and their role in keeping information secure is critical. For example, educating employees on how to identify and report phishing schemes or how important it is to maintain a secured Wi-Fi network at their remote office is key to implementing a secure hybrid workplace.
IBM i Security Considerations
For IBM i companies, there are some unique security requirements, according to Moshe Sofer, our partner at Raz-Lee Security. Keeping your IBM i systems safe and secure against possible attacks is crucial to creating a comprehensive hybrid workplace security strategy.
To ensure that the environment is safe and has the micro-security controls needed to implement a successful zero trust approach, IT managers must pay particular attention to these issues:
- To keep the system safe, companies need to isolate, secure and control all network-connected devices. It’s especially important to control which devices can connect to IBM i. You must secure and segment networks, isolate network assets and control communications among them. This includes sign-on, FTP connections and other exit points. By exploiting existing vulnerabilities on the IBM i platform, users can perform an unauthorized activity using remote TCP/IP applications, protocols and services designed to connect to the server remotely. A native IBM i firewall solution must control access based on multiple factors, including the user, their permissions, their working schedule and the devices with which they have connected. This must combine seamlessly with specific multifactor authentication for IBM i that can work with any authentication app.
- You need methodologies to classify and categorize data combined with technology solutions for securing and managing the data, including encryption in transit and at rest. For data in transit, you need a tool that ensures PGP encryption. For data at rest, you need to use FIELDPROC. Files must be encrypted from source to target, between different platforms, environments and devices, with the highest level of efficiency and accountability.
- Further strategies must limit and enforce users’ access, including technologies continuously monitoring and governing access privileges. Users’ authority levels must be continually controlled. Any authority elevation must be temporary and not permanent. The right policies and tools can enable an organization to control this and easily audit authorities and privileges, significantly lowering the risk of a cyberattack.
Incorporating these hybrid workplace security requirements for IBM i will ensure the trust and compliance companies depend on.
Creating a Hybrid Workplace Security Strategy
Follow these steps to build your cybersecurity hybrid workplace strategy:
- Perform a hybrid workplace security strategy assessment. Evaluate your current cybersecurity strategy and how it addresses the potential hybrid workplace risks for key IBM i and non-IBM i applications and data that need to be protected, including compliance and audit requirements.
- Document new security technology and solution requirements for IBM i and non-IBM i cybersecurity within the hybrid workplace security strategy assessment.
- Evaluate your company’s current security solutions and their support for a hybrid workplace. Does your IAM solution incorporate a trust factor to ensure that the authenticated user is trusted and secure as they access systems from across town or the country?
By understanding the requirements and risks associated with a hybrid workplace, IBM i companies can ensure their continued security, trust and compliance.